Transform Security with Zero Trust Network Access Quotes
As you explore the evolving landscape of cybersecurity, embracing Zero Trust Network Access (ZTNA) could be the key to fortifying your digital defenses, so browse options to see how this innovative approach can revolutionize your security strategy today.
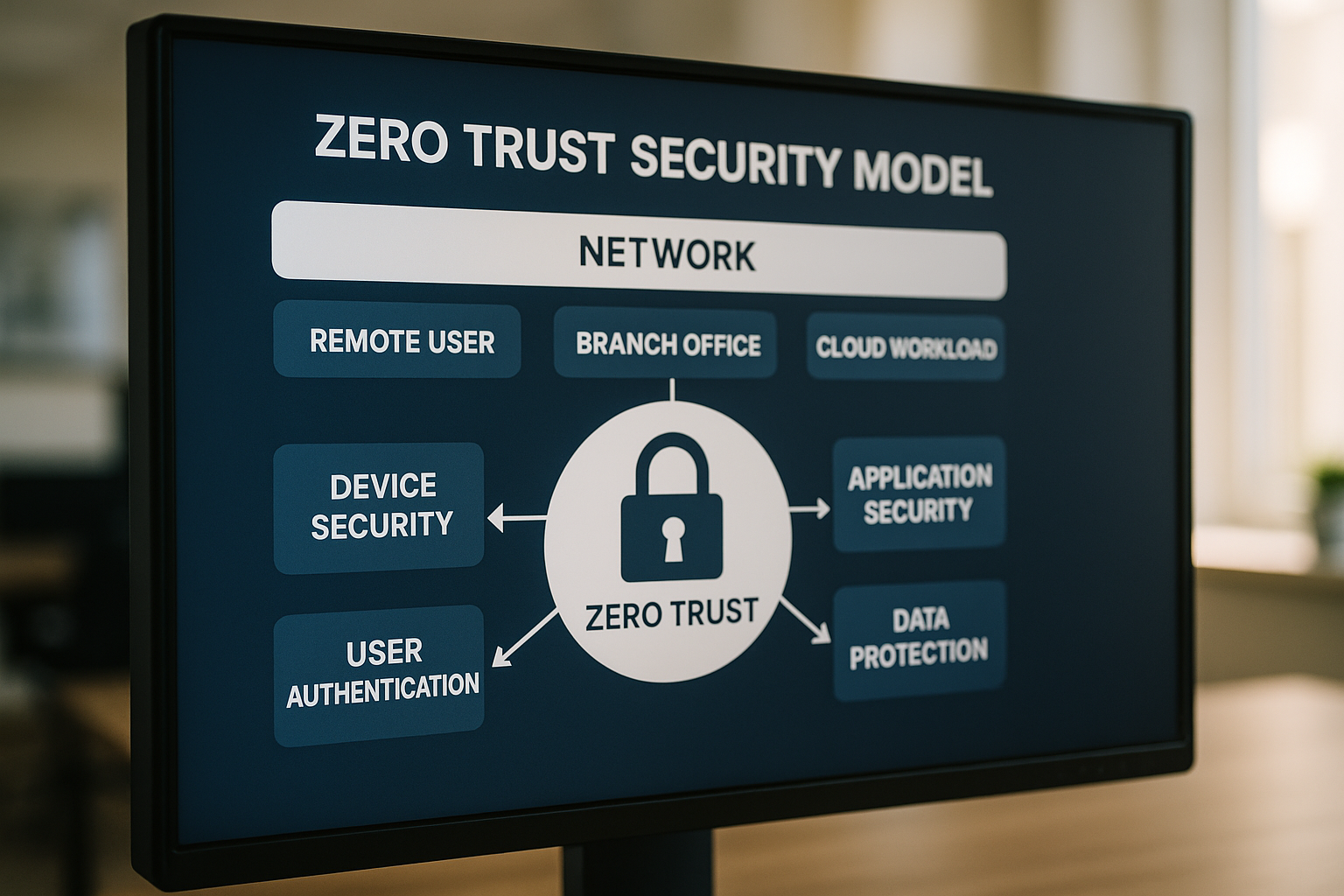
Understanding Zero Trust Network Access
Zero Trust Network Access (ZTNA) is a security model that fundamentally shifts the traditional approach to network security by eliminating the assumption of trust within a network. Instead of automatically trusting devices or users inside the network perimeter, ZTNA requires continuous verification of every access attempt, regardless of where it originates. This model is particularly relevant in today's digital environment, where remote work and cloud services are prevalent.
ZTNA operates on the principle of "never trust, always verify," ensuring that only authenticated and authorized users can access specific resources. This approach significantly reduces the risk of unauthorized access and data breaches. By implementing ZTNA, organizations can effectively safeguard sensitive information, even as their networks grow more complex and distributed.