Revolutionize security forever zero trust network access revealed
If you're looking to transform your organization's security framework into a robust, future-proof model, then exploring the innovative world of Zero Trust Network Access (ZTNA) is the next logical step—browse options, search options, and see these options to ensure your network remains impenetrable.
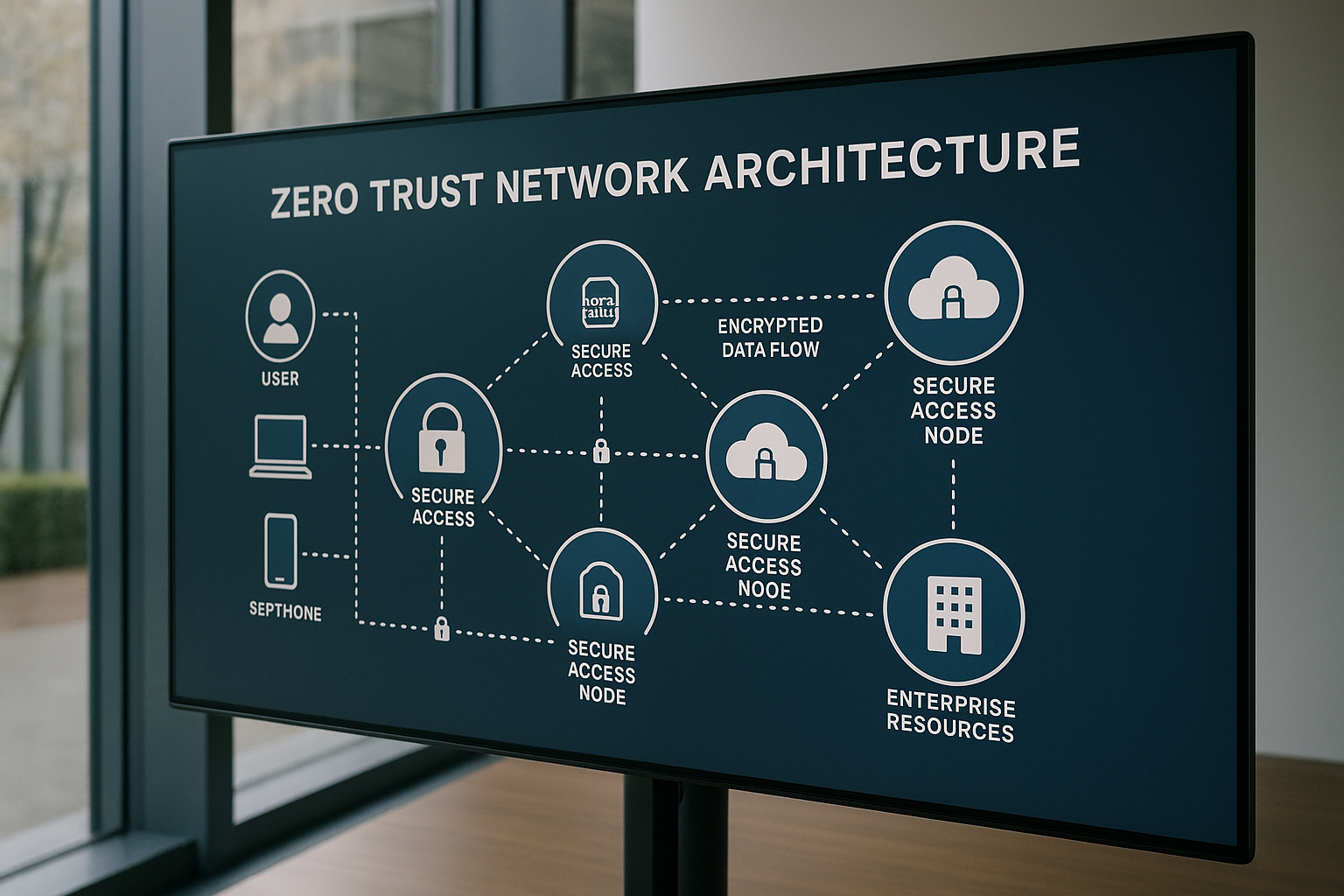
Understanding Zero Trust Network Access
Zero Trust Network Access (ZTNA) represents a paradigm shift in cybersecurity, moving away from traditional perimeter-based defenses to a more granular, identity-centric approach. Unlike conventional methods that trust users once they are inside the network, ZTNA operates on the principle of "never trust, always verify," ensuring that every access request is authenticated, authorized, and encrypted before granting entry1.
The Benefits of Implementing ZTNA
Adopting ZTNA offers a multitude of advantages. Firstly, it significantly reduces the risk of data breaches by minimizing the attack surface. Each user is granted access solely to the resources they need, effectively containing potential threats2. Furthermore, ZTNA enhances remote work security, a critical feature in today's hybrid work environments. By ensuring secure connections regardless of location, organizations can maintain productivity without compromising security3.
Cost Implications and Financial Considerations
While the initial implementation of ZTNA may require investment in new technologies and training, the long-term savings are substantial. By preventing costly data breaches and reducing the need for extensive on-premise infrastructure, organizations can achieve significant cost efficiencies. Moreover, many vendors offer scalable solutions that can be tailored to the specific needs of businesses, allowing for flexible pricing models that align with budget constraints4.
Real-World Applications and Success Stories
Numerous organizations have successfully integrated ZTNA into their security strategies, reporting enhanced security postures and operational efficiencies. For example, a leading financial institution implemented ZTNA to secure its remote workforce, resulting in a 30% reduction in security incidents within the first year5. Similarly, a global technology firm leveraged ZTNA to streamline its access management processes, improving user experience and reducing administrative overhead6.
Exploring ZTNA Solutions
For organizations considering a transition to ZTNA, numerous specialized services and solutions are available. Leading cybersecurity firms offer comprehensive ZTNA platforms that integrate seamlessly with existing IT infrastructure, providing a smooth transition to this advanced security model. As you explore these options, ensure you evaluate vendors based on their ability to deliver scalable, user-friendly solutions tailored to your specific needs.
Incorporating Zero Trust Network Access into your cybersecurity strategy not only fortifies your defenses but also positions your organization at the forefront of security innovation. As you browse options and explore available solutions, consider how ZTNA can transform your security posture, ensuring resilience and peace of mind in an increasingly complex digital landscape.